A few weeks ago, I got to play around with a Tandbard RDX® QuikStor™. I tried to convince the SBS Backup Assistant to recognize the device as a backup target which unfortunately did not work right away. Using google I came across quite a few people who are having the same problem and most of those got either the same answer “It’s not supported and does not work” or they got a hint to use wbadmin as the command-line tool works unlike the assistant. The thing with this is that the SBS Console does not recognize it when you backup like this and it will actually tell the user that there is no backup configured.
There is a way though to get it working like it should. The thing is the backup assistant does not show removable media as a backup target and only shows fixed disks. And this is there the RDX Utility of Tandberg comes into play. Using the utility you can switch the device mode from “removable” to “fixed disk”. Just double-click on your device and go to the “Utility” tab. Here you can click on “Change device mode”.
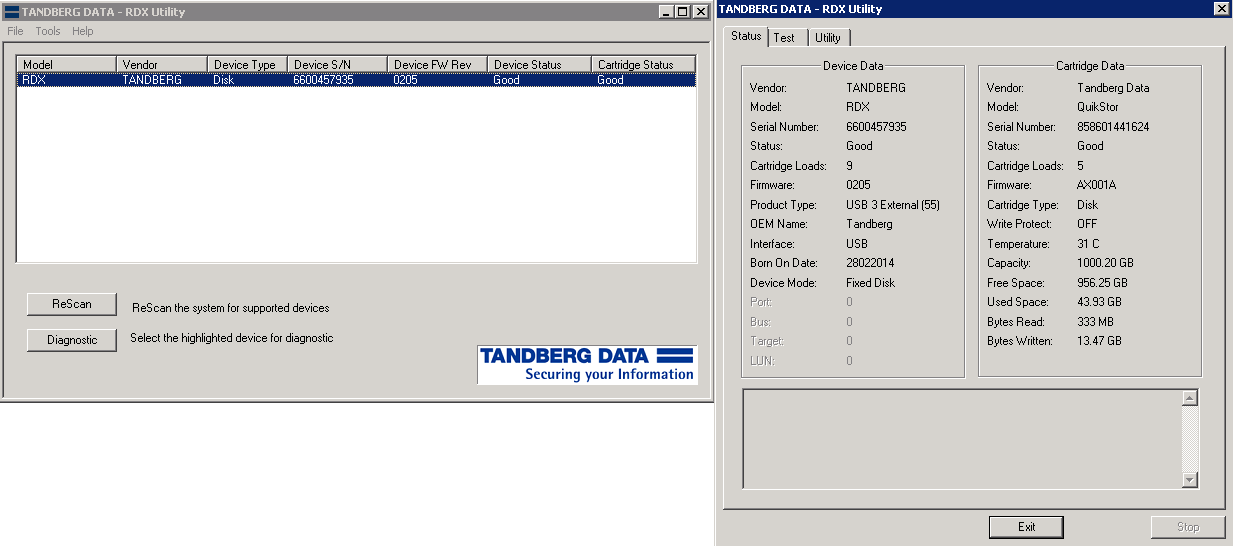
Having done this you can now use a single cartridge as backup target. So you want to use multiple cartridges and the assistant won’t let you? For this you need to use the commandline-tool wbadmin to configure multiple targets. You can use “wabadmin get disks” to list all disks available as backup-target and then use “wbadmin enable backup –addtarget:” to add it to the backup. The error message in the screenshot below only tells me that I had already added the disk to the backup-targets.
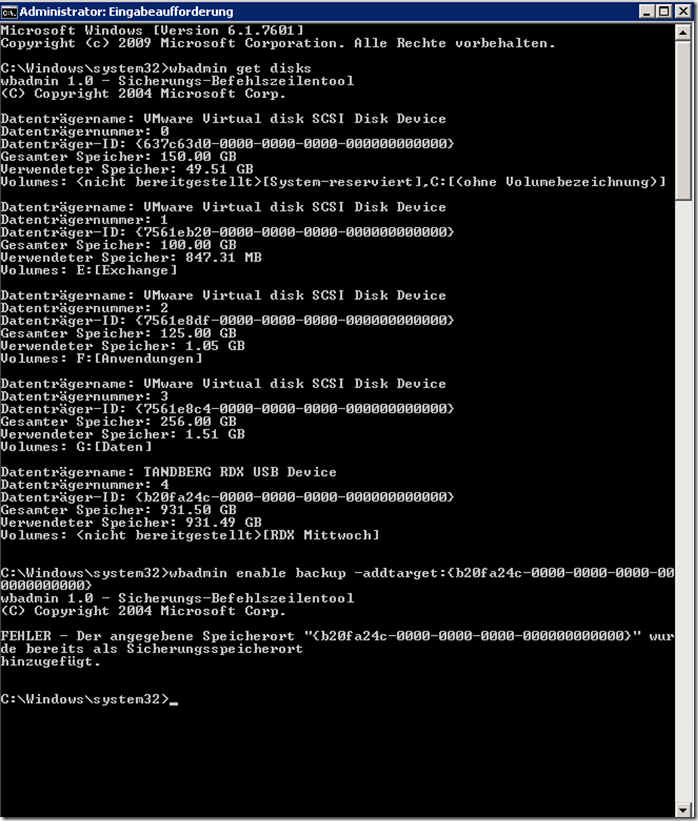
There is one caveat to doing this though. The RDX device in “removable media” mode will prevent you from ejecting the cartridge when there is activity on the device and instead the LED will blink orange a few times. When in “fixed disk” mode it will not do that and eject the cartridge. You can imagine what will happen if you do this while a backup is running. So make sure you swap cartridges only when the backup is complete. I scheduled the backup to run two hours after the last employee left the building and told the customer to swap the cartridges when leaving and not in the morning when coming to work as the backup might still be running (and it sometimes is). Also, when using multiple cartridges you will have to do full backups and cannot use differentials.
Posted by lsmooth on 2014/06/29 at 11:15 AM under Allgemein.
Tags: Backup, RDX, SBS, Server Essentials, Tandberg, Windows Server Backup
Comment on this post.
Imagine the following scenario:
Within a domain-network you want to provide a service, that can only be accessed by your domain-users, without them having to login. Take for example Typo3 on a host running linux with Apache. The required modules and libraries for apache and kerberos have already been installed and configured and you are currently trying to get kerberos to work. A domain-account has been created and a keytab was provided for the linux-host to use.
But if kinit now keeps displaying the error “Client not found in kerberos database” this can have several reasons. The Linux-Host could have a wrong hostname. So if for example the principal in the keytab was created for HTTP/cms.example.org@EXAMPLE.ORG but the Linux-Host has the hostname typo3.example.org the above error-message can be displayed.
Also, general typos while creating the keytab can be responsible. But if you have already ruled out such mostly easy to spot mistakes, then most of the time the Windows Event Log on the KDC can help. If you for example find the event ID 11 with source KDC saying “There are multiple accounts with name HTTP/cms.example.org of type DS_SERVICE_PRINCIPAL_NAME.” what exactly does that mean? It means that the principal that you created has been asssigned to multiple accounts.
A principal for a service is assigned to an account using the attribute servicePrincipalName of that account. So you can assign the same principal to multiple accounts which is not allowed. Such a mistake can be corrected using LDP. You just look for the accounts in question and remove the attribute servicePrincipalName from those accounts where you don’t need it (anymore). Using LDP the filter servicePrincipalName=HTTP/cms* with BaseDN DC=example,DC=org. After correcting the attributes you can simply try to get a ticket using kinit.
Posted by lsmooth on 2013/11/29 at 2:16 AM under Allgemein.
Tags: Active Directory, Kerberos, Linux
Comment on this post.
Ever had one of those Rogue-AVs or Fake-AVs or know someone who had? Not so bad you think? Read on and think again 😉
So, two days ago I got called by an employee of one of our customers. He said he was searching the web for an explanation of a word and since then could not use his computer anymore because trying to start any program would result in a popup telling him that his software was infected by a variant of conficker. I headed over there to take a look at his computer and what I found was this:
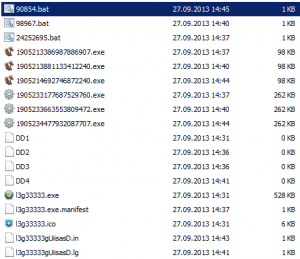
The one that was causing the popups was
l3g33333.exe – MD5 96a8901b0ff0c49bbb7bf9b5221f1399
But what caught my eye were the other 6 binaries in that folders:
1905213386987886907.exe – MD5 a20ad23e771da6c10554f3410b91439d
1905213881133412240.exe – MD5 a20ad23e771da6c10554f3410b91439d
1905214692746872240.exe – MD5 93018c83adf8b4ea6067e791a33f82e4
1905233177687529760.exe – MD5 4bafa135003d6843ba3b87c1dbdc8901
1905233663553809472.exe – MD5 4bafa135003d6843ba3b87c1dbdc8901
1905234477932087707.exe – MD5 4bafa135003d6843ba3b87c1dbdc8901
Needless to say I took a sample to examine the binaries and the first file I examined was 1905213386987886907.exe. The file was compressed using Mystic Compressor. I unpacked the file manually and started to examine the unpacked PE with IDA freeware and here is what I found.
The sample harvests passwords from all common and some not so common software like ssh-clients, ftp-clients, email-clients and webbrowsers. It also tries to collect certificates with OID 2.5.29.37 which are usable for code-signing, and client- and server-authentication and tries to export their private keys from windows certificate store.
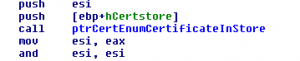
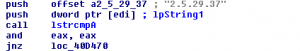
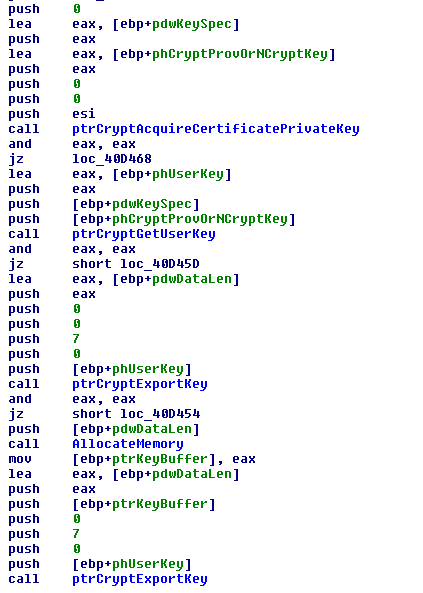
The sample also contains a list of passwords possibly already harvested from other victims. The password list is used to try to logon as other users in Windows Terminal Server and Active Directory environments and also harvest their passwords and certificates. The collected data is then sent to a server using a POST-request to hxxp://115.47.49.181/xSZ64Wiax/ojXVZBxRQVfp6gAUziCGnB8V7Aikbs0Z.php.
I did not take a too close look into the sample, just the parts that immediatly caught my eye. When you caught this one there’s a really high chance that all your credentials (passwords and certificates) are gone and need to be changed asap.
I will examine the other samples in the next days to check out what they’re up to.
Posted by lsmooth on 2013/09/29 at 9:15 PM under Malware Analysis.
Tags: Certificate, FakeAV, IDA Pro, Malware, Password, RogueAV
Comment on this post.
So, while doing IT support for quite a few customers, I occasionally come across workstations infected different kinds of malware. Usually I clean up those infections. I know “Don’t do that, wipe it and reinstall” you say. But most small companies won’t pay or can’t afford that. So I remove those more or less nasty things.
Every now and then I put a copy of the malware on my thumbdrive to reverse engineer it. While doing that sometimes I come across a piece of malware that loads most of its imports at runtime. Some of those use hashes for the names of windows api functions. Instead of using LoadLibrary and GetProcAddress they use LoadLibrary (some also use the PEB for kernel32 or ntdll) to load libraries and calculate hashes on the exported functions.
Continue reading ‘APIhasher’ »
Posted by lsmooth on 2013/04/09 at 8:29 PM under Tools.
Tags: Imports, Tools, Windows-API
Comment on this post.